Introduction
The Internet of Things (IoT) has revolutionized the way we live, offering convenience and connectivity like never before. From smart homes to wearable devices, IoT has become an integral part of our daily lives. However, with this increased connectivity comes the risk of cyber vulnerabilities. As more and more devices become connected, the potential for security breaches and data theft also increases. In this blog post, we will explore the various cyber vulnerabilities associated with IoT devices and discuss ways to stay protected.
The Rise of IoT Devices
IoT devices have gained immense popularity due to their ability to enhance convenience and efficiency. These devices, ranging from smart thermostats to fitness trackers, are designed to collect and exchange data through the internet. By connecting to other devices and systems, IoT devices offer seamless automation and control.
The Vulnerabilities
While IoT devices offer numerous benefits, they also present significant security risks. Here are some common vulnerabilities associated with IoT devices:
1. Weak Authentication
Many IoT devices come with default usernames and passwords, which are often weak and easily guessable. This makes it easier for hackers to gain unauthorized access to these devices and exploit their functionalities.
2. Lack of Encryption
Encryption plays a crucial role in securing data transmitted between IoT devices and their connected systems. However, many devices lack proper encryption protocols, making them susceptible to eavesdropping and data breaches.
3. Outdated Firmware
Manufacturers often release firmware updates to address security vulnerabilities. However, users frequently neglect to update their IoT devices, leaving them exposed to known threats that could have been mitigated.
4. Insecure Network Connections
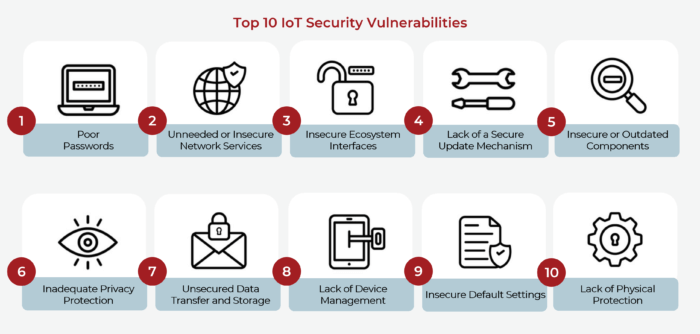
IoT devices rely on network connections to communicate and exchange data. Weak or unsecured networks can be easily compromised, allowing hackers to intercept and manipulate the transmitted information.
Protecting Your IoT Devices
While the risks associated with IoT devices cannot be completely eliminated, there are several measures you can take to enhance their security:
1. Change Default Credentials
One of the simplest yet most effective steps is to change the default usernames and passwords of your IoT devices.
Summary
As IoT devices continue to proliferate, it is crucial to understand the potential cyber vulnerabilities they pose. These vulnerabilities can range from weak passwords and unencrypted data transmission to insecure firmware and lack of regular security updates. Hackers can exploit these weaknesses to gain unauthorized access to devices, compromise personal information, and even launch large-scale attacks.
To stay protected, it is essential to take proactive measures. This includes securing your home network, using strong and unique passwords, regularly updating device firmware, and being cautious about the data you share with IoT devices. Additionally, investing in reliable security solutions, such as firewalls and antivirus software, can provide an extra layer of protection.
Furthermore, manufacturers and developers play a crucial role in ensuring the security of IoT devices. They should prioritize security during the design and development stages, implement robust encryption protocols, and provide regular security updates to address any discovered vulnerabilities.
In conclusion, while IoT devices offer numerous benefits, it is important to be aware of the cyber vulnerabilities they can introduce. By taking proactive measures and staying in check out this site formed about the latest security practices, we can enjoy the convenience of IoT devices while minimizing the risks associated with cyber threats.
- Q: What are IoT devices?
- A: IoT devices, or Internet of Things devices, are physical objects embedded with sensors, software, and connectivity capabilities to collect and exchange data over the internet.
- Q: What are cyber vulnerabilities?
- A: Cyber vulnerabilities refer to weaknesses or flaws in the security of a system or device that can be exploited by cybercriminals to gain unauthorized access, steal data, or disrupt operations.
- Q: How can I protect my IoT devices from cyber vulnerabilities?
- A: To protect your IoT devices, you should:
- Change default passwords and use strong, unique passwords for each device.
- Regularly update the firmware and software of your devices to patch any security vulnerabilities.
- Disable unnecessary features and services that are not being used.
- Segment your network to isolate IoT devices from critical systems.
- Use a firewall to filter incoming and outgoing traffic.
- Monitor your devices for any suspicious activity or signs of compromise.
- Q: What are some common cyber vulnerabilities in IoT devices?
- A: Common cyber vulnerabilities in IoT devices include:
- Weak or default passwords that are easily guessable.
- Lack of encryption for data transmission, making it easier for attackers to intercept and manipulate the data.
- Outdated or unpatched software/firmware with known security vulnerabilities.
- Insecure network connections or protocols.
- Lack of proper authentication and authorization mechanisms.
- Insufficient physical security measures.
- Q: What are the potential risks of not securing IoT devices?
- A: Not securing IoT devices can lead to various risks, including:
- Unauthorized access to sensitive data.
- Privacy breaches and data leaks.
- Malware infections and botnet participation.
- Disruption of critical services or infrastructure.