Overcoming Data Security Concerns in the Cloud
Introduction
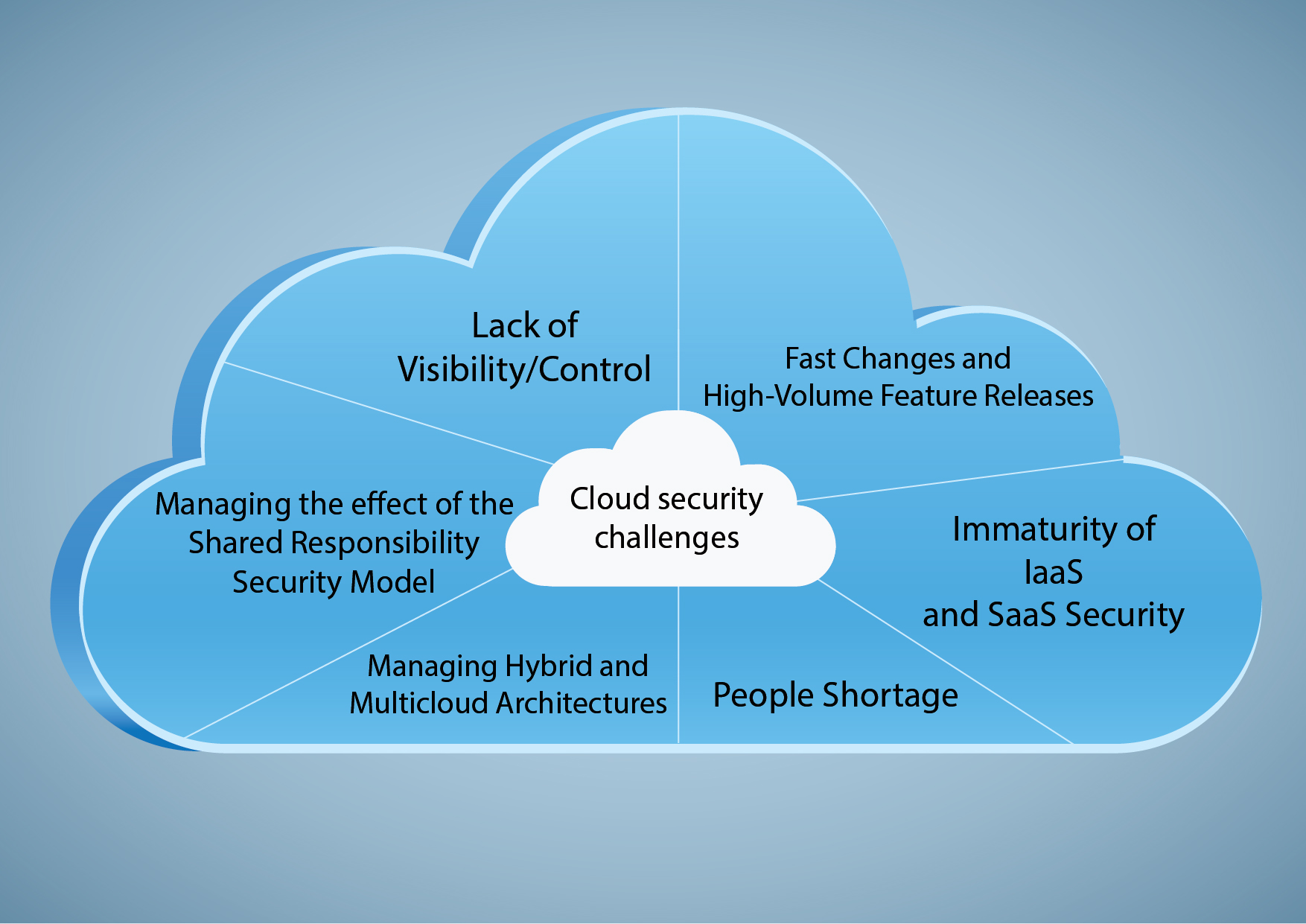
Data security is a critical aspect of any organization’s operations, especially when it comes to storing and managing data in the cloud. As more businesses embrace cloud computing for its scalability, cost-effectiveness, and flexibility, concerns about the security of sensitive information have become increasingly prevalent. In this blog post, we will explore some common data security concerns associated with cloud computing and discuss effective strategies to overcome them.
1. Choose a Reliable Cloud Service Provider
When selecting a cloud service provider, it is crucial to opt for a reputable and reliable company. Look for providers that have a strong track record in data security and offer robust encryption methods. Additionally, ensure that the provider complies with industry standards and regulations to guarantee the safety of your data.
2. Implement Strong Authentication Measures
One of the primary concerns in cloud security is unauthorized access to data. To mitigate this risk, implement strong authentication measures such as multi-factor authentication (MFA). MFA adds an extra layer of security by requiring users to provide multiple forms of identification, such as a password and a unique code sent to their mobile device.
3. Encrypt Your Data
Encrypting your data is an essential step in securing it in the cloud. Encryption converts your data into an unreadable format, making it inaccessible to unauthorized individuals. Use strong encryption algorithms and ensure that your encryption keys are stored separately from the data to enhance security.
4. Regularly Update and Patch Systems
Cloud service providers often release updates and patches to address security vulnerabilities. It is crucial to regularly update your systems and applications to ensure that you have the latest security features and fixes. Failure to update your systems may leave them vulnerable to attacks.
5. Implement Data Loss Prevention (DLP) Measures
Data loss prevention measures help prevent sensitive information from being leaked or lost. Implement DLP solutions that monitor and control data movement within the cloud environment. These solutions can detect and prevent unauthorized sharing of data, ensuring that your information remains secure.
6. Conduct Regular Security Audits
Regular security audits are essential to identify any vulnerabilities or weaknesses in your cloud infrastructure. Conduct thorough assessments to evaluate your security controls, identify potential risks, and implement necessary improvements. “Overcoming Data Security Concerns in the Cloud
Summary
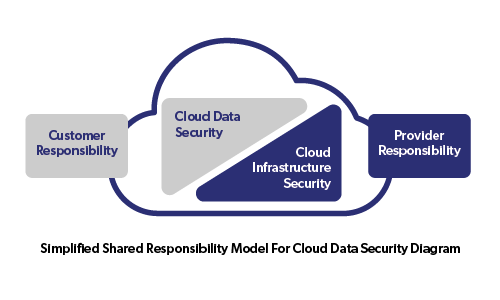
Cloud computing offers numerous benefits, but it also introduces unique challenges in terms of data security. Organizations must address concerns such as unauthorized access, data breaches, and compliance issues to ensure the safety and integrity of their data. This blog post will delve into various strategies that can help overcome these concerns, including implementing strong access controls, encrypting data, regularly monitoring and auditing cloud environments, and choosing reputable cloud go to my site service providers. By adopting these measures, businesses can confidently leverage the power of the cloud while safeguarding their valuable data.
- Q: What are some common data security concerns in the cloud?
- A: Common data security concerns in the cloud include unauthorized access, data breaches, data loss, lack of control over data, and compliance with regulations.
- Q: How can I ensure data security in the cloud?
- A: To ensure data security in the cloud, you can implement strong access controls, encrypt your data, regularly backup your data, use multi-factor authentication, and choose a reputable cloud service provider.
- Q: What is data encryption and how does it help in cloud security?
- A: Data encryption is the process of converting data into a coded form that can only be accessed with a decryption key. It helps in cloud security by ensuring that even if the data is intercepted, it remains unreadable without the proper key.
- Q: How can I protect my data from unauthorized access in the cloud?
- A: You can protect your data from unauthorized access in the cloud by using strong passwords, implementing role-based access controls, regularly monitoring access logs, and regularly updating your security measures.
- Q: What measures can I take to prevent data breaches in the cloud?
- A: To prevent data breaches in the cloud, you can regularly update your software and systems, conduct regular security audits, educate your employees about security best practices, and implement intrusion detection and prevention systems.
- Q: How can I ensure compliance with data protection regulations in the cloud?
- A: To ensure compliance with data protection regulations in the cloud, you should choose a cloud service provider that offers compliance certifications, implement proper data access controls, regularly audit your data security practices, and stay updated with the latest regulations.

Hello, I’m Brayden Denman, a passionate and experienced Mobile App Developer specializing in Cloud Computing, Software Development, Mobile App Integration, and AI & Machine Learning. With a strong background in these fields, I strive to create innovative and user-friendly solutions that meet the ever-evolving needs of businesses and individuals.
Introduction Data security is a critical aspect of any organization’s operations, especially when it comes to storing and managing data in the cloud. As more businesses embrace cloud computing for its scalability, cost-effectiveness, and flexibility, concerns about the security of sensitive information have become increasingly prevalent. In this blog post, we will explore some common…

Hello, I’m Brayden Denman, a passionate and experienced Mobile App Developer specializing in Cloud Computing, Software Development, Mobile App Integration, and AI & Machine Learning. With a strong background in these fields, I strive to create innovative and user-friendly solutions that meet the ever-evolving needs of businesses and individuals. Read More.
Recent Posts
- Challenges in Cross-Platform Digital Asset Search and Retrieval
- The Role of AI in Enhancing Digital Asset Retrieval
- Implementing Automation in Digital Asset Recovery Processes
- Digital Asset Retrieval: Addressing Security and Privacy Concerns
- Optimizing Metadata for Quicker Digital Asset Discovery
- Overcoming Barriers in Searching and Accessing Digital Assets
- Best Practices for Efficient Digital Asset Retrieval
- Harnessing the Power of Deep Learning: A Beginner’s Guide
- Scalability Issues in Large-Scale Machine Learning Projects
- Navigating the Ethical Challenges of AI Implementations
